What is Cyber Security ?
Cyber security refers to the body of technologies, processes, and practices designed to protect networks, devices, programs, and data from attack, damage, or unauthorized access. Cyber security may also be referred to as information technology security.
•Real-time Website Security Monitoring
•Email Server Security Review
•Managed Endpoint Detection & Response
•Penetration Test – Network / Web
•Internal Network Vulnerability Assessment
•Incident Management Setup
•External Network Vulnerability Assessment
•Hardening Checks
•Drafting Security Policies
VULNERABILITY ASSESSMENT AND PENETRATION TESTING
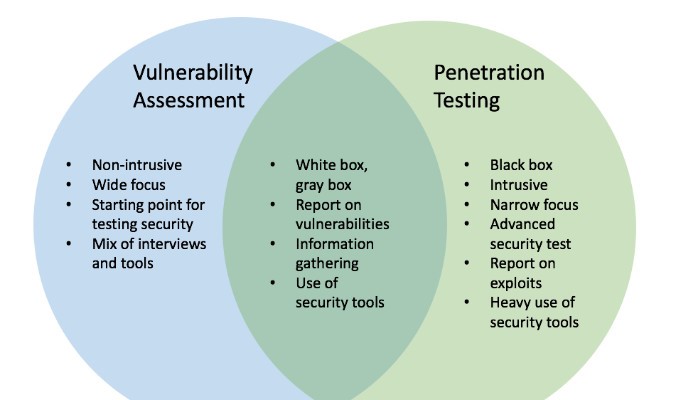
Vulnerability Assessment
Vulnerability analysis, also known as vulnerability assessment, is a process that defines, identifies, and classifies the security holes (vulnerabilities) in a computer, network, or communications infrastructure. In addition, vulnerability analysis can forecast the effectiveness of proposed countermeasures and evaluate their actual effectiveness after they are put into use
Penetration testing
Penetration testing aims to identify vulnerabilities and risks in the system which may impact the confidentiality, integrity, and availability of the data by emulating a real attack.
In this approach, the organization employs security analysts who work as hackers (ethical hackers) to identify the uncovered security loopholes. The only thing that separates a penetration tester from an attacker is permission.
Benefit from Vulnerability Assessment
•Data protection and empowering businesses to better shield its systems from malicious attacks
•Reduce the cost of security breaches.
Good reputation in front of clients, as your clients also want their information stays protected.
•Concrete action plan based on the report to ensure security of existing and new technologies.
Benefit from Penetration testing
•Identify and resolve system vulnerabilities
•Gain valuable insights into your digital systems
•Establish trust with your clientele
